Today, let’s talk about rats. Not the long-tailed rodents, but the digital kind – Remote Access Trojans, or RATs. These are Trojans that attackers use to gain remote access to a device. Typically, these RATs can install and uninstall programs, control the clipboard and log keystrokes.
In May 2024, a new breed of RAT, SambaSpy, wandered into our rat trap. To learn how this malware infects its victims’ devices and what it does once it’s inside, read on.
What SambaSpy is
SambaSpy is a feature-rich RAT Trojan obfuscated using Zelix KlassMaster, making it much more difficult to detect and analyze. However, our team was up to the challenge and discovered that this new RAT is capable of:
- Managing the file system and processes
- Downloading and uploading files
- Controlling the webcam
- Taking screenshots
- Stealing passwords
- Loading additional plug-ins
- Remotely controlling the desktop
- Logging keystrokes
- Managing the clipboard
Impressed? It seems SambaSpy can do it all – the perfect tool for a 21st century James Bond villain. But even this extensive list isn’t exhaustive: read more about this RAT’s capabilities in the full version of our study.
The malicious campaign we uncovered was exclusively targeting victims in Italy. You may be surprised, but this is actually good news (for everyone except Italians). Threat actors usually try to cast a wide net to maximize their profits, but these attackers are focused on just one country. So why is that a good thing? It’s likely that the attackers are testing the waters with Italian users before expanding their operation to other countries – and we’re already one step ahead, since we’re familiar with SambaSpy and how to counter it. All that our users worldwide need to do is make sure they have a reliable security solution, and read on knowing that we’ve got this.
How attackers spread SambaSpy
In short, just like many other RATs, via email. The attackers used two primary infection chains, both involving phishing emails disguised as communications from a real estate agency. The key element in the email is a CTA to check an invoice by clicking a hyperlink.
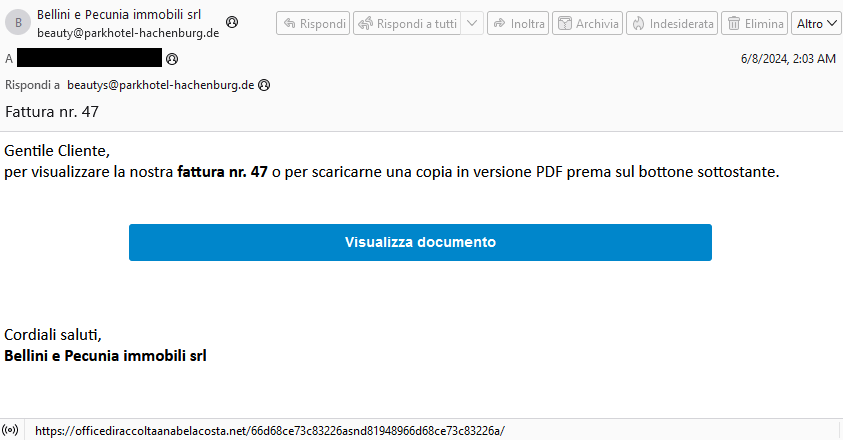
At first glance, the email appears legitimate – except that it’s sent from a German email address, but written in Italian
Clicking the link redirects users to a malicious website that checks the system language and the browser used. If the potential victim’s OS is set to Italian and they open the link in Edge, Firefox or Chrome, they receive a malicious PDF file that infects their device with either a dropper or a downloader. The difference between the two is minimal: the dropper installs the Trojan immediately, while the downloader first downloads the necessary components from the attackers’ servers.
Before starting, both the loader and the dropper check that the system isn’t running in a virtual machine and, most importantly, that the OS language is set to Italian. If both conditions are met, the device is infected.
Users who don’t meet these criteria are redirected to the website of FattureInCloud, an Italian cloud-based solution for storing and managing digital invoices. This clever disguise allows the attackers to target only a specific audience – everyone else is redirected to a legitimate website.
Who’s behind SambaSpy?
We’ve yet to determine which group is behind this sophisticated distribution of SambaSpy. However, circumstantial evidence has shown us that the attackers speak Brazilian Portuguese. We also know that they’re already expanding their operations to Spain and Brazil – as evidenced by malicious domains used by the same group in other detected campaigns. By the way, these campaigns no longer include the language check.
How to protect yourself from SambaSpy
The key takeaway from this story is the method of infection, which suggests that anyone, anywhere, speaking any language could be the target of the next campaign. For the attackers, it doesn’t really matter who they hit, nor are the particulars of the phishing bait important. Today, it might be an invoice from a real estate agency; tomorrow, a tax notification; and the day after that, airline tickets or travel vouchers.
Here are a few tips and recommendations to help you stay safe from SambaSpy:
- Install Kaspersky Premium before your device shows any signs of infection. Our solution reliably detects and neutralizes both SambaSpy and other malware.
- Always be wary of phishing emails. Before you click on a link in your inbox, take a moment to ask yourself: “Could this be a scam?”
 RAT
RAT

 Tips
Tips